12:06 PM 4/16/2021 - M.N.: The shooting site with the telling name of "Indianapolis FedEx Ground-Plainfield Operations Center" is within the close walking-running-driving distance to and from the airport. Is this why it was chosen? | The National Interest: Is Azerbaijan’s Ilham Aliyev the new Saddam Hussein?
M.N.: The shooting site with the telling name of "Indianapolis FedEx Ground-Plainfield Operations Center" is within the close walking-running-driving distance to and from the airport. Is this why it was chosen? "Veni, vidi, vici" ... NO TRACES ...
This investigative hypothesis and lead have to be considered.
12:06 PM 4/16/2021 - Post Link
_______________________________________________
indystar.com/story/news/cri…
| Michael_Novakhov shared this story . |
The gunman who killed eight people at an Indianapolis FedEx facility parked his vehicle, got out of his car and quickly began randomly shooting, police said during a 10:30 a.m. news conference.
Police did not identify the killer or any victims, but said the gunman used a rifle. Four of the victims were found outside the facility and four were found inside. Five others were injured and transported from the scene, four of them with non-fatal gunshot wounds, IMPD Deputy Chief Craig McCartt said.
The gunman killed himself inside the facility before officers arrived, McCartt said. The incident lasted a matter of minutes, McCartt said.
“This suspect came to the facility and when he came there, he got out of his car and pretty quickly started some random shooting outside the facility," McCartt said. "There was no confrontation with anyone that was there. There was no disturbance. There was no argument. He just appeared to randomly start shooting. And that began in the parking lot, and then he did go into the building, into the facility, for a brief period of time before he took his own life."
Additional details were scarce at the news conference, which also included comments from Indianapolis Mayor Joe Hogsett, IMPD Chief Randal Taylor and FBI Special Agent in Charge Paul Keenan.
Police said they had some leads that led them to an unidentified residence. Keenan said the FBI was "assisting on the search of the suspect's home."
Hogsett said White House Chief of Staff Ron Klain had reached out via text message to offer assistance. Klain is a North Central High School graduate.
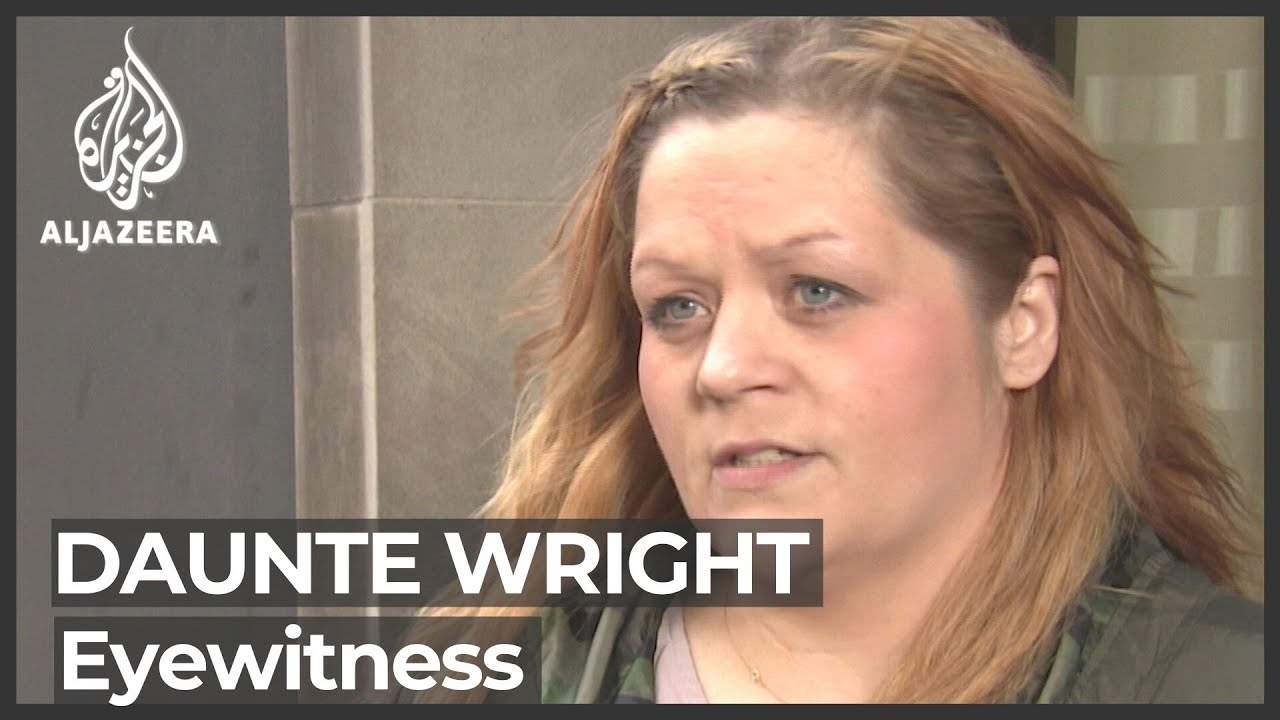
The shooting at the FedEx Ground Plainfield Operations Center near the Indianapolis International Airport late Thursday night was the largest mass shooting in Indianapolis in at least the past 15 years.
This story will be updated.
'Senseless, horrific':What officials are saying about FedEx shooting in Indianapolis
FedEx shooting:What we know about the mass shooting in Indianapolis
Gun control:Indy council member calls on lawmakers to address gun control after FedEx shooting
Contact IndyStar reporter Tony Cook at 317-444-6081 or tony.cook@indystar.com. Follow him on Twitter: @IndyStarTony.
Call IndyStar reporter Amelia Pak-Harvey at 317-444-6175 or email her at apakharvey@indystar.com. Follow her on Twitter @AmeliaPakHarvey.
Contact Lawrence Andrea at 317-775-4313 or landrea@indystar.com. Follow him on Twitter @lawrencegandrea.
The Department of Justice issued a press release Tuesday that raised eyebrows: The FBI had obtained a warrant from a federal judge authorizing them to search and seize – to delete copies of – malicious software that had been surreptitiously installed in privately owned servers used to manage emails using Microsoft Exchange. The noteworthy part: The FBI was removing the malware first, and attempting to notify the servers’ owners after the fact. This approach is almost unprecedented.
The backstory captured in the documents was revealing. The FBI affidavit supporting the warrant application had been filed under seal on April 9, and a redacted version was posted with the press release. The affidavit laid out the case for the warrant: Malicious actors, known in the infosec community as HAFNIUM and believed to be associated with the Chinese government, had launched a widespread attack on Microsoft Exchange servers. The attack exploited a zero-day, or previously unknown, vulnerability and used it to install a webshell, which enabled the hackers to remotely access the servers. Once the webshells were installed, those backdoors could be used by the hackers to carry out a range of other malicious actions, including downloading additional malware, exfiltrating information, and prepositioning other attacks using those servers or credential information stolen from them as the launch point for follow-on attacks.
In early March, Microsoft announced the vulnerability and made patches available. However, the FBI’s analysis indicated that a number of infected servers had not been cleaned – and, importantly, the naming convention for the webshells was both predictable in its pattern and unique to each individual server, meaning that the FBI could assess which webshells were still intact. But these webshells were difficult for many server-owners – who likely include small businesses as well as local governments, nonprofits, and organizations of all kinds – to detect and remove. According to some estimates, as many as 60,000 Exchange servers may have been affected, and the FBI’s assessment was that “most of these victims are unlikely to remove the remaining web shells because the web shells are difficult to find due to their unique file names and paths or because these victims lack the technical ability to remove them on their own.”
With that in mind, the FBI tested a method for removing the webshells without the server owners’ knowledge or consent. It then had that methodology validated by an external expert to ensure that there were no indications of damage to the system or any of its legitimate (non-malicious) software. With those steps completed, the FBI sought and obtained approval to proactively remove the malware from each of the servers where it could be detected – in other words, to search for the evidence of the crime, and seize the evidence (the malicious webshell software) where it could be found.
All of these facts matter to an overall understanding of what was at stake here, and why this operation was a suitable one for a criminal search and seizure warrant. In legal and policy analysis, finding the right analogy is always important. Here, the analogy (which I shared with a reporter for Wired in this piece) can be likened to a bomb threat: If the FBI knows that an organized criminal syndicate has planted bombs on private property across multiple states, and those bombs are armed and could go off at any time, the FBI is going to take swift action to find and neutralize those devices – especially if it’s difficult for property owners to detect them. In exigent circumstances like these, law enforcement would be justified in entering directly onto the private property in order to neutralize the bombs and seize the evidence.
The nature of this remote access malware is, from a cyber threat perspective, like an armed bomb: It can be activated at any time, and it can cause irreparable destruction to property. Based on the government affidavit and press release, it’s clear that DOJ believed they knew enough about the cyber actor behind this exploit to assess that there was a real and pressing risk that the webshells would be used to cause further damage. Plausible scenarios include launching ransomware, exfiltrating personally identifiable and other sensitive information, harvesting credentials, carrying out business email compromise attacks, and more. Given these risks, and the property owner’s inability to remediate them quickly, DOJ essentially took the position that the FBI needed to step in and defuse the bombs before they went off.
Of course, from a Fourth Amendment perspective, in truly exigent circumstances such as imminent danger, the government doesn’t need a search warrant to act. Here, the government obtained a warrant – but the subtext of its application was that an active cyber intrusion into a significant number of servers, hosting a commonly used email software program and all of the associated user data, presented an urgent threat to the integrity of those systems and the data residing on them, as well as to the broader ecosystem of data and accounts that were connected to those servers or accessible from the credentials contained on them. To put it another way: When a nation-state actor has achieved remote access to thousands of email servers around the country, the federal government needs to step in to help neutralize and remove the ticking software time-bombs that could imperil entire sectors of the economy.
It’s a bold and innovative use of the authorities granted to the government under the Federal Rules of Criminal Procedures, making creative use of the provisions in FRCrimP 41(6)(b)(6). Rule 41(6)(b)(6), revised in 2016, allows courts to issue warrants authorizing law enforcement “to use remote access to search electronic storage media and to seize or copy electronically stored information” as part of an investigation into cybercrimes. The reality is that a wide range of businesses and organizations use Microsoft Exchange, and not all of them will have the resources or sophistication to identify and eradicate an exploit of the kind described in the affidavit. And for every server left compromised, there’s a risk that the installed webshell could be used to propagate further and more lasting harm, both against that victim and – using their server — data or credentials as the launch point or foundation – against others.
We don’t know what decision-making process went on behind the scenes before the government applied for this warrant. But I’ve suggested below a non-exhaustive list of factors that the government should take into account when deciding whether to seek similar authorization in the future:
- Does the exploit at hand currently impact, or have the potential to impact, hardware or software that is in common, widespread use by individuals and entities who are likely to have varying levels of resource and sophistication to detect, combat, and remediate cyber threats?
- How widespread has the exploit become?
- Is the exploit one that makes it an effective launching point for follow-on operations against these or other victims?
- Is the exploit one that has been launched by a nation-state or non-state actor who may be seeking to use it for strategic advantage with national security or geopolitical implications?
- Is the exploit one for which advisory notices, patches, or similar remediations have been announced but the exploit clearly still persists?
- Is the exploit one which the government can identify with precision in each particular instance for which it proposes undertaking a search and seizure action?
- Can the search and seizure be accomplished without causing harm to other hardware, software, or data on the affected system?
- What level of testing or external review can the government take, or has it undertaken, to validate its assumptions about likelihood of unintended harm?
- Do the overall circumstances suggest a degree of urgency which argues in favor of government action under FRCrimP 41(6)(b)(6), rather than notifying and obtaining approval from system owners individually in advance?
Each of these factors will likely have a range of possible outcomes; none of these factors are likely to be dispositive in and of themselves; and more factors will likely emerge over time as the government considers future operations that are similar to this one. And to be clear: At the moment, there is nothing in the federal rules, case law, or other precedent that requires the government to undertake this kind of internal, multi-factor review prior to filing an application for a search and seizure warrant under Rule 41(6)(b)(6). But given the power of this tool, and the inevitable and appropriate concern about potential misuse, the government would be wise to formulate such a multi-factor test, and to make its guidelines, or at least a summary of them, public.
After all, privacy and security advocates are right to point to the potential risks for the government to misuse this kind of access authorization. However, the reality on the ground is that the private sector has been clamoring for years for the government to take a more active role in protecting private networks from malicious cyber activity – and these calls for a more proactive government approach have been echoed in congressional hearings, as well as blue-ribbon commissions like the Cyberspace Solarium Commission. This operation was an example of one way that the government might do that.
With that in mind, for those who might argue that the FBI’s action creates an unacceptable risk of overreach, it would be prudent to get a reaction from the business community, and particularly from those whose servers were involved in the FBI action. Were the business owners who were notified after the fact grateful for the FBI’s action, or did they view it as overly intrusive? Are there professional or trade associations within or across industries who are willing to take a position on this, and do they support these actions or not? Opinion polls and position papers won’t affect the underlying legality of the warrant or operation, but they may serve as significant indicators of the extent to which similar operations are perceived as legitimate and appropriate cyber defense tools in the future.
So, were the government’s actions helpful? Based on the information available right now: the answer is yes. The recent SolarWinds hack serves as a stark and compelling reminder of the way in which cybersecurity incidents can have staggering breadth and scope. DOJ’s transparency on this HAFNIUM search and seizure operation is important, and future operations will be benefitted by even more transparency. Critical components of that transparency will include openness about whether the FBI or DOJ have a set of guidelines or parameters that they rely on in assessing other similar operations in the future and, if so, what those criteria are. But in an era of ever-heightening cyber risk, and against a backdrop of repeated requests and recommendations from countless corners for expanded government action to assist the private sector, this operation is an innovative and important step.
Image: A signage of Microsoft is seen on March 13, 2020 in New York City. Photo by Jeenah Moon/Getty Images
The post We’re from the Government, We’re Here to Help: The FBI and the Microsoft Exchange Hack appeared first on Just Security.
Kris Osborn
Ukraine Conflict, Europe

As tensions mount over Ukraine and the Russian buildup on its border, concerns are being raised by some Russian media outlets about possible alleged Ukrainian terrorist attacks.
As Russia maneuvers troops and weapons into possible attack formations along its border with Ukraine and concern mounts about a potential invasion, there does also appear to be an uptick in Russian-driven information warfare as well.
In what could be viewed as a clear attempt to justify and encourage support within Russia for a possible invasion of Ukraine, Russia’s TASS newspaper can an article claiming that Ukrainian terrorists are plotting attacks against Russia. Citing plots of “sabotage” and “terrorism” in Crimea.
The TASS piece quotes Russian Security Council Secretary Nikolai Patrushev saying, “Ukraine’s intelligence agencies and extremist groups constantly carry out provocations on the state border and attempt to conduct acts of sabotage and terrorism in Crimea, notably at critical infrastructure facilities.” Citing Western “sponsors,’ Patrushev directed inflammatory rhetoric at the United States and the North Atlantic Treaty Organization (NATO), saying “the destructive activity of the US, and the NATO bloc controlled by it, a number of EU states, Ukraine, aimed at discrediting Russia’s domestic and foreign policy, harming its authority and international image, and disseminating extremist and nationalist ideology.”
The Russian propaganda points to what it called “militants from abroad,” who had fought for Ukraine during Russia’s 2014 invasion, calling Ukrainian fighters “international terrorists.” In the TASS article, Patrushev claimed that over the last year, six terror attacks and ten terror-related crimes were thwarted and twenty-three extremism-associated crimes were foiled in Crimea.
“Centers for training saboteurs have been established in Ukraine with the West’s support, Patrushev noted. “At its Western sponsors’ behest, centers for training sabotage and reconnaissance groups have been set up in Ukraine. It is not ruled out that the graduates of these centers will focus on plotting terror attacks, and not only in Russia but also in other states,” he stated, according to the report.
Although Russia is not a democracy, the Russian citizenry and leadership are certainly greatly impacted by public opinion and prevailing beliefs regarding the actual extent of any threat. Therefore, it might clearly be in Moscow’s interest to massively exaggerate any actual Ukrainian-inspired terrorist threat to Russia. Meanwhile, the Security Service of Ukraine is reporting that the Ukrainian military is itself conducting anti-terrorism drills near the Russian border. “The SBU will launch multi-stage anti-terrorism drills in the Kharkov Region on April 14. The exercises will be taking place across the region until the end of May with a focus on border areas,” a statement from the SBU reads. The exercises are intended to closely replicate actual combat conditions, with troops using firearms, military equipment and radio-electronic devices.
Finally, in that TASS article, Patrushev claimed that on April 9, 2021, another terror attack plotted by supporters of the Hayat Tahrir al-Sham international terrorist organization (outlawed in Russia) was prevented in Simferopol.
Kris Osborn is the defense editor for the National Interest. Osborn previously served at the Pentagon as a Highly Qualified Expert with the Office of the Assistant Secretary of the Army—Acquisition, Logistics & Technology. Osborn has also worked as an anchor and on-air military specialist at national TV networks. He has appeared as a guest military expert on Fox News, MSNBC, The Military Channel, and The History Channel. He also has a Masters Degree in Comparative Literature from Columbia University.
Image: Reuters.
Michael Rubin
Security, Middle East

Dictators have their own strategies to distract and deceive the United States with charm, charisma, caviar and cocktails.
Azerbaijani Ilham Aliyev is proud. On April 12, 2021, Azerbaijani public television station ITV broadcast an hour-long program inaugurating a new museum in Baku to celebrate Azerbaijan’s victory in the forty-four-day Nagorno-Karabakh War. Aliyev, who never served in the military even as his peers fought in the first Nagorno-Karabakh War, strolls around in military fatigues showing off captured Armenian equipment and wax models of Armenian soldiers before addressing assembled troops. The centerpiece of the “Park of Trophies” is an arch made from the helmets of killed and captured Armenian soldiers. That Azerbaijan continues to hold illegally 260 prisoners of war (POWs) and kidnapped civilians, some of whom it might have killed in captivity, underscores the tastelessness of the display.
Aliyev is not the first to construct such a display. In his 1991 work The Monument, a study of the public art of a totalitarian society, Kanan Makiya, the son of a famous architect and a prominent Iraqi intellectual, profiled the “Victory Arch,” known to locals as the Swords of Qadisiyah. Commissioned in 1985 and opened four years later, the monument, which stands taller than the Arc de Triomphe in Paris, consisted of forearms molded from Saddam Hussein’s own and fists holding crossed swords made from steel derived from the melted weaponry of fallen Iraqi soldiers. Five thousand Iranian helmets taken off the battlefield completed the monument. Hussein’s speech initiating its construction was little different from Aliyev’s: “Brave Iraqis have recorded the most legendary exploits in defense of their land and holy beliefs,” Hussein declared on April 22, 1985. “We have chosen that Iraqis will pass under their fluttering flag protected by their swords which have cut through the necks of the aggressors.” Aliyev, for his part, declared at the park’s inauguration on Monday, “Everyone who visits the park of military trophies will see the strength of our army, will see our willpower, and how hard it was to achieve victory.” As for POWs, I was the Pentagon Iraq desk officer on duty when the mass graves of Kuwaiti prisoners whom Hussein had seized were found.
The similarities between Hussein and Aliyev are increasingly hard to dismiss. Years before he became an avowed enemy, Hussein intrigued the State Department who saw him as a pragmatic moderate. In an April 1975 meeting, for example, Assistant Secretary of State Alfred Atherton for Near Eastern Affairs told Secretary of State Henry Kissinger, “Hussein is a rather remarkable person . . . he’s a very ruthless and—very recently, obviously—pragmatic, intelligent power.” The United States holds much the same assessment toward Aliyev.
In 1983, President Ronald Reagan dispatched Donald Rumsfeld, at the time a former secretary of defense, to meet with Hussein. Rumsfeld was impressed. “I began to think that through increased contacts we might be able to persuade the Iraqis to lean toward the United States and eventually modify their behavior,” he recalled. Undersecretary of State Lawrence Eagleburger told Hussein’s envoy not to take seriously American condemnation of chemical weapons. The recent history of the Minsk Group shows U.S. officials likewise seemingly downplaying concerns about Azeri violations of its international agreements.
In both cases, the State Department was willing to ignore the treatment of minorities. When reports surfaced regarding Hussein’s use of chemical weapons against Iraq’s Kurdish population, one American diplomat explained, “The approach we want to take is that, ‘We want to have a good relationship with you, but that this sort of thing makes it very difficult.’” Meanwhile, the State Department remains silent as Aliyev calls the Armenian genocide false.
There has also been a similar sense of dictator chic surrounding Hussein’s Iraq and Aliyev’s Azerbaijan. In December 1985, the Washington Post Magazine gave a swooning account of a dinner party hosted by Iraqi ambassador Nizar Hamdoon whose outreach was targeting influential Jewish American and pro-Israeli figures. Today, the Azerbaijani embassy in Washington regularly targets the same audience. Journalists and diplomats both recognize Aliyev’s “caviar diplomacy.”
Both Hussein and Aliyev also sought glory through territorial conquest while blaming their victims. When Hussein bragged about decapitating Iranian aggressors, he omitted that Iraq started the war with a surprise attack. Likewise, Aliyev suggests that Armenians were the aggressors when it was Azeri forces, in conjunction with Turkish support, who launched a multipronged, surprise attack on Nagorno-Karabakh on the centennial anniversary of the Ottoman invasion of Armenia. Both Hussein and Aliyev were also irredentists. American diplomats dismissed Hussein’s repeated statements that Kuwait was a wayward Iraqi province as rhetoric excess right up to Iraq’s surprise invasion of Kuwait; today, the State Department ignores Aliyev’s statements laying claim to the entirety of Armenia.
The parallels go further. While diplomats considered both Hussein and Aliyev secular moderates, both sought to channel Islamist extremism to their benefit. Years before the Islamic State beheaded women deemed un-Islamic, the Fedayeen Hussein would decapitate women, many professionals, whom the Baathist regime deemed “prostitutes” for refusing to veil. During the most recent conflict, Aliyev imported and dispatched Al Qaeda-linked mercenaries from Syria.
Enumerating the similarities between Hussein and Aliyev is not just an intellectual exercise, but rather a warning. While the State Department debates its strategies toward other countries, seldom does it recognize that dictators have their own strategies to distract and deceive the United States with charm, charisma, caviar and cocktails. They believe Americans naïve for allowing themselves to be distracted by a paper-thin patina while they pursue other agendas. Should American officials continue to calibrate policy to the style of Azeri officials rather than the reality of their policies, however, the world will likely see another war of aggression by Azerbaijan, just as Hussein launched his own against Kuwait more than three decades ago.
Michael Rubin is a resident scholar at the American Enterprise Institute (AEI). You can follow him on Twitter: @mrubin1971.
Image: Reuters

- White House: Intel on Russian 'bounties' on US troops shaky The Associated Press
- What civilians in Afghanistan say about America's withdrawal CNN
- The End of the United States’ Forever War The New York Times
- Washington can prevent a humanitarian disaster after we leave Afghanistan | TheHill The Hill
- By pulling troops from Afghanistan, Biden risks a humanitarian disaster | Trudy Rubin The Philadelphia Inquirer
- View Full Coverage on Google News
A gunman killed eight people and then apparently turned his weapon on himself at a FedEx facility in Indianapolis on April 15. Read more: https://wapo.st/3gaDALg. Subscribe to The Washington Post on YouTube: https://wapo.st/2QOdcqK
Follow us:
Twitter: https://twitter.com/washingtonpost
Instagram: https://www.instagram.com/washingtonpost/
Facebook: https://www.facebook.com/washingtonpost/


 audio/mp3 a.mp3
audio/mp3 a.mp3СМОТРИМ В HD ТУТ 👉 - https://smotrim.ru/vesti/?utm_source=youtube&utm_medium=all&utm_campaign=all_0
Подпишитесь на канал Россия24: https://www.youtube.com/c/russia24tv?sub_confirmation=1
Помощник президента России Юрий Ушаков пообщался с послом США Джоном Салливаном. Он сообщил американскому дипломату о мерах, которые Москва примет в ответ на введенные Вашингтоном санкции.
Последние новости России и мира, политика, экономика, бизнес, курсы валют, культура, технологии, спорт, интервью, специальные репортажи, происшествия и многое другое.
#Россия24 #Вести #Новости
Официальный YouTube канал ВГТРК.
Россия 24 - это единственный российский информационный канал, вещающий 24 часа в сутки. Мировые новости и новости регионов России. Экономическая аналитика и интервью с влиятельнейшими персонами.
Смотрите также:
Вести недели с Дмитрием Киселевым - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaTpipoWQNR1ya5zp19Gc4ZB
Вести в субботу с Сергеем Брилевым - https://www.youtube.com/playlist?list=PL6MnxjOjSRsQAPpOhH0l_GTegWckbTIB4
Воскресный вечер с Владимиром Соловьевым - https://www.youtube.com/playlist?list=PLwJvP0lZee7zYMGBmzUqNn16P71vHzgkU
60 минут - https://www.youtube.com/channel/UCR16nHT1nkmG7g9AkE9tGeQ?sub_confirmation=1
Новости в прямом эфире - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaQ73BA1ECZR916u5EI6DnEE
Международное обозрение - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaSEmz_g88P4pjTgoDzVwfP7
Специальный репортаж - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaQLdG0uLyM27FhyBi6J0Ikf
Интервью - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaReDfS4-5gJqluKn-BGo3Js
Факты - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaR4eBu2aWmjknIzXn2hPX4c
Мнение - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaST71OImm-f_kc-4G9pJtSG
Россия и мир в цифрах - https://www.youtube.com/playlist?list=PLLHjKKyQ4OaRx4uhDdyX5NhSy5aeTMcc4
A gunman shot at least eight people dead and injured several others at a FedEx facility in Indianapolis before taking his own life, police said early on Friday.
#News #Reuters #FedexShooting #IndianapolisFedexShooting #Fedex #Indianapolis
Subscribe: http://smarturl.it/reuterssubscribe
Reuters brings you the latest business, finance and breaking news video from around the globe. Our reputation for accuracy and impartiality is unparalleled.
Get the latest news on: http://reuters.com/
Follow Reuters on Facebook: https://www.facebook.com/Reuters
Follow Reuters on Twitter: https://twitter.com/Reuters
Follow Reuters on Instagram: https://www.instagram.com/reuters/?hl=en

Al Jazeera has spoken to an eyewitness who says the police did not give Daunte Wright immediate medical care after he was shot by an officer.
The 20-year-old had been stopped by police for a minor traffic violation in the state of Minnesota on Sunday.
Al Jazeera's Shihab Rattansi reports from Minneapolis, Minnesota.
- Subscribe to our channel: http://aje.io/AJSubscribe
- Follow us on Twitter: https://twitter.com/AJEnglish
- Find us on Facebook: https://www.facebook.com/aljazeera
- Check our website: https://www.aljazeera.com/
#AlJazeeraEnglish #UnitedStates #DaunteWright



Comments
Post a Comment